# Fraktal AWS Audit
This app allows you to audit and monitor your Amazon Web Services (AWS) assets for configuration weaknesses and security vulnerabilities automatically and continuously. It has been created in collaboration with our partner Fraktal Ltd, the experts in AWS security.
The app connects to your AWS account(s) with your consent. It then employs AWS Config, AWS Security Hub and Amazon GuardDuty to scan your AWS assets periodically, and provides you with alerts about any critical identified weaknesses and vulnerabilities in your configurations.
The instructions below explain the installation of the app, integration with your AWS environment, how to enable AWS Config, AWS Security Hub and AWS GuardDuty functionalities, and how to grant the minimum permissions for the app to scan your AWS assets.
When the app identifies vulnerabilities, it will provide you with details of the finding and a link to the AWS console to find out more. If you would like to receive expert assistance to mitigate or fix the findings, you can contact Fraktal Ltd (opens new window) for their professional services.
# Install the Fraktal AWS Audit app
Open the Fraktal AWS Audit (opens new window) app page.
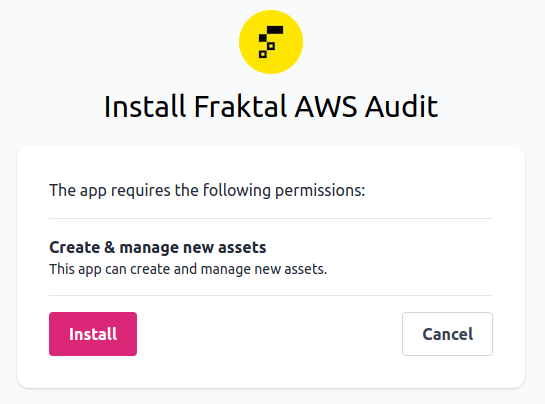
Install the app.
The app asks for permission to connect to your AWS account and to create assets to Badrap based on your AWS environment.
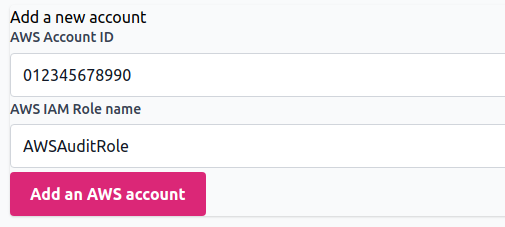
Enter your AWS Account ID (opens new window) into the
Account IDfield.Create a recognizable role name for the app, e.g. "AWSAuditRole".
Note down the "External-ID" value that the app creates. You will need it later when creating a role delegation in the AWS console.
# Create AWS role
Configure role delegation for the app with the AWS IAM console.
Create a new role in the AWS IAM console (opens new window).
Select
Another AWS accountfor the role type.Enter
816084135002(AWS Audit app Account ID) as theAccount ID.Check the
Require external IDoption, and enter the External ID that the app generated for you earlier.Leave the
Require MFAoption unchecked.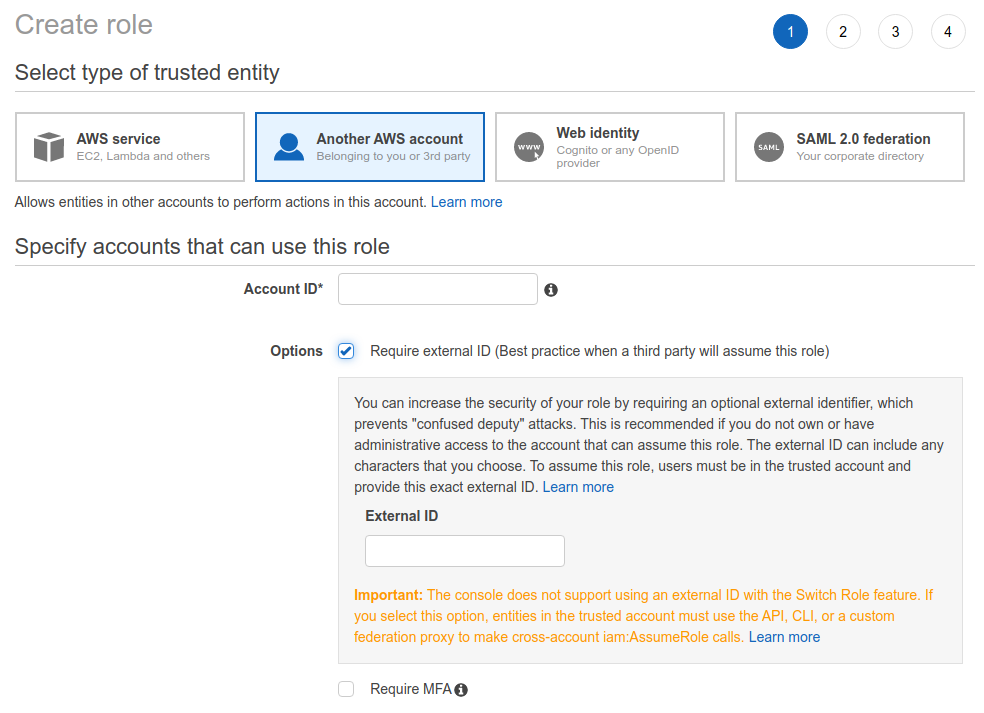
Click
Next: Permissions.Type
ReadOnlyAccessto the policy search bar, scroll down to find the correct policy and select it.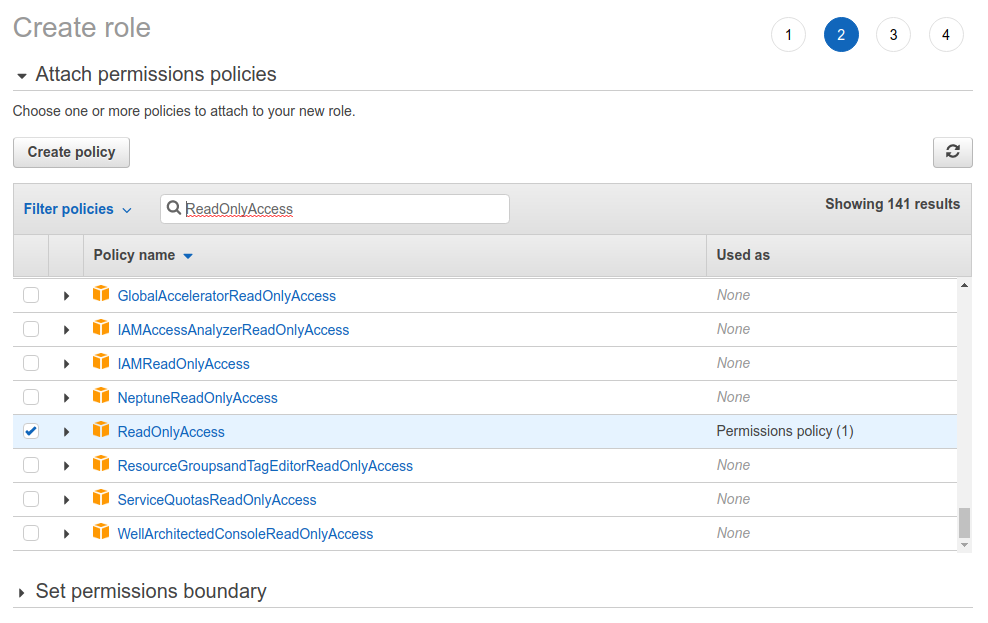
Type
SecurityAuditto the policy search bar, scroll down to find the correct policy and select it.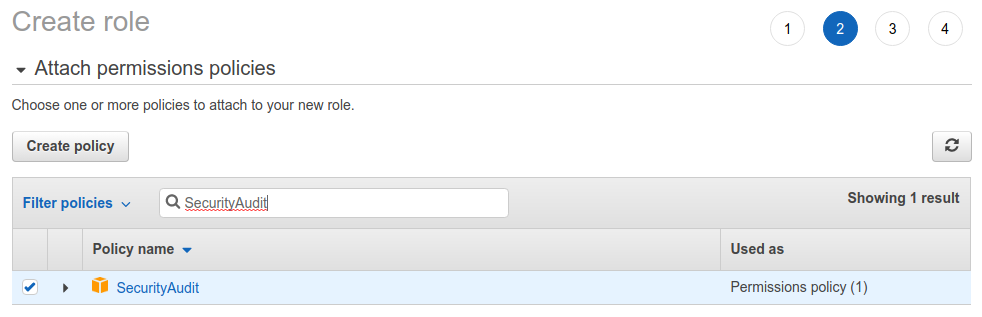
Click
Next: Tags.Click
Next: Review.Name the role (e.g.,
AWSAuditRole).Click
Create role.
# Enable AWS Config
The app integrates with Amazon's tools AWS Config, Security Hub and GuardDuty to monitor for weaknesses and vulnerabilities in your configurations. You need to enable these features in your AWS console for the app to function properly. First, let's go through how to enable AWS Config.
Go to the AWS Config (opens new window) setup page in AWS Console.
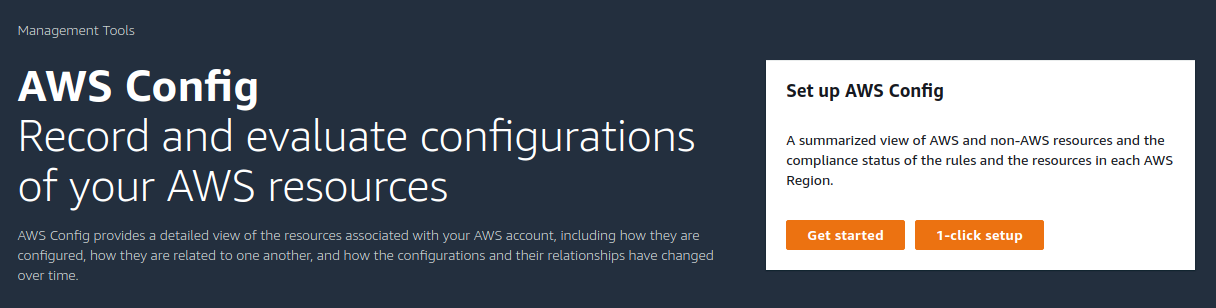
Select your AWS region (e.g. eu-north-1) from the drop-down menu in the right upper corner.
Review the pricing for AWS Config, and then click on either "1-Click setup" or "Get started" to enable and configure AWS Config for your selected region.
Review the configuration and click "Confirm" to enable AWS Config.
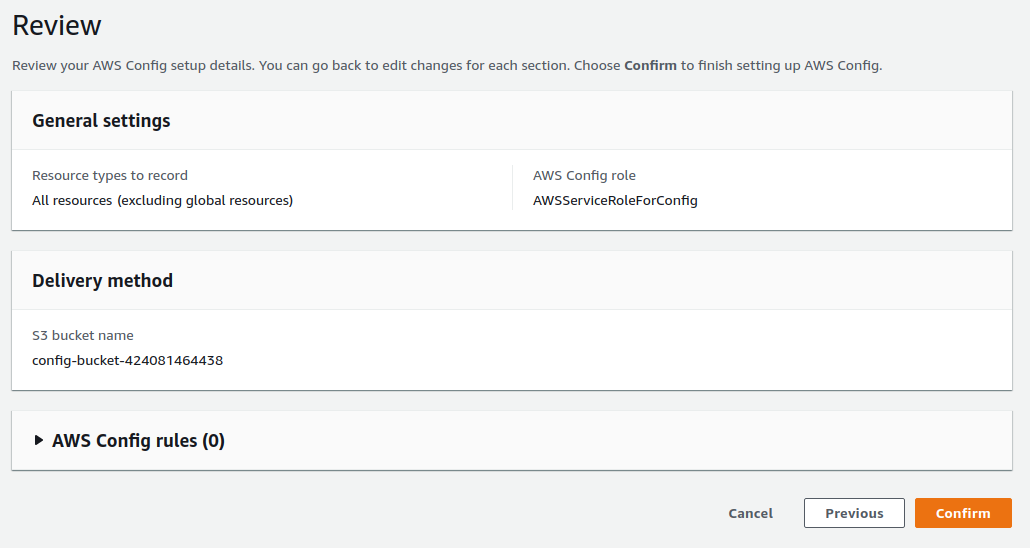
AWS Config is required before you can enable AWS Security Hub or Amazon GuardDuty (next steps).
# Enable AWS Security Hub
AWS Security Hub performs checks for security best practices. It automatically detects services that are configured in a way that leaves them vulnerable to attacks. It categorizes its findings into those that need immediate attention and those that can be dealt with later. Let's go through how to enable AWS Security Hub for your AWS services.
Go to the AWS Security Hub (opens new window) setup page in AWS Console.
Select your AWS region (e.g. eu-north-1) from the drop-down menu in the right upper corner.

Review the pricing, and then click on "Go to Security Hub" to enable and configure AWS Security Hub for your selected region. Make sure to turn on "Enable AWS Foundational Security Best Practices" and "Enable CIS AWS Foundations Benchmark".
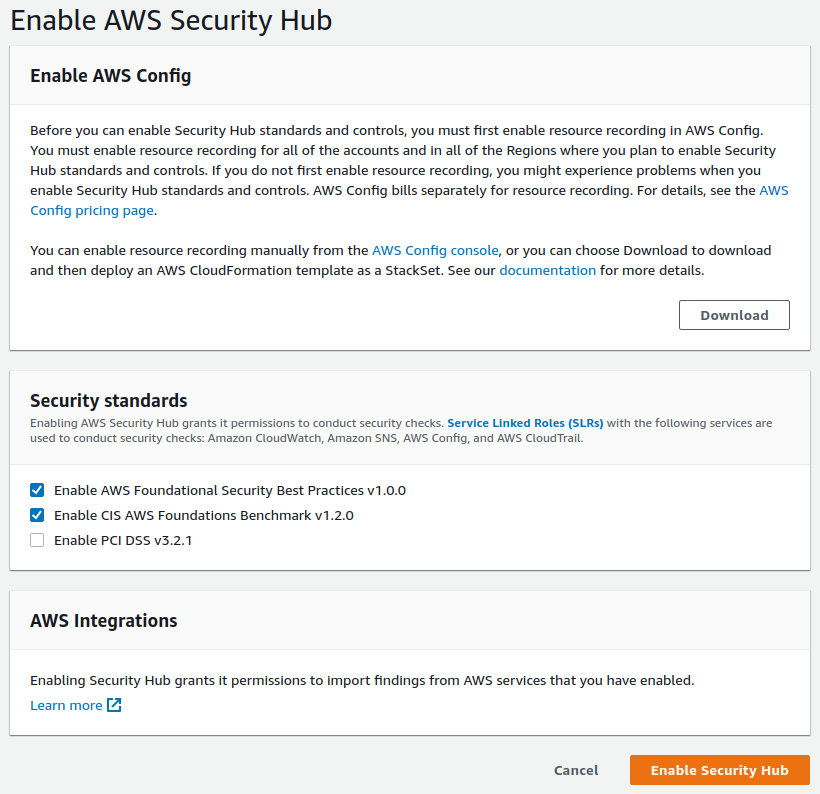
Note that it may take up to a few hours before all of the compliance checks of AWS Security Hub are enabled.
# Enable Amazon GuardDuty
Amazon GuardDuty continuously monitors your AWS account for malicious activity and unauthorised behaviour. Whereas AWS Security Hub is more concerned about compliance and configurations, GuardDuty is more concerned about the runtime behaviour of your systems. You should use both of them to get the best possible results on both configuration and runtime security of your environment. Let's see how to enable Amazon GuardDuty.
Go to the Amazon GuardDuty (opens new window) setup page in AWS Console.
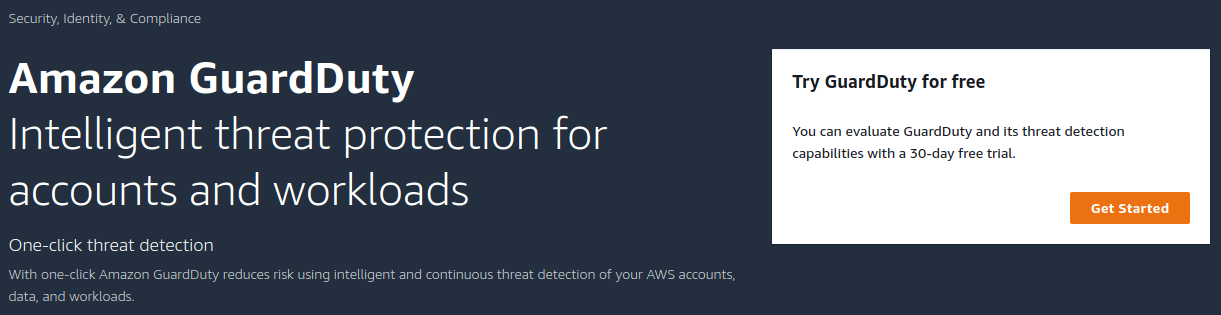
Select your AWS region (e.g. eu-north-1) from the drop-down menu in the right upper corner.

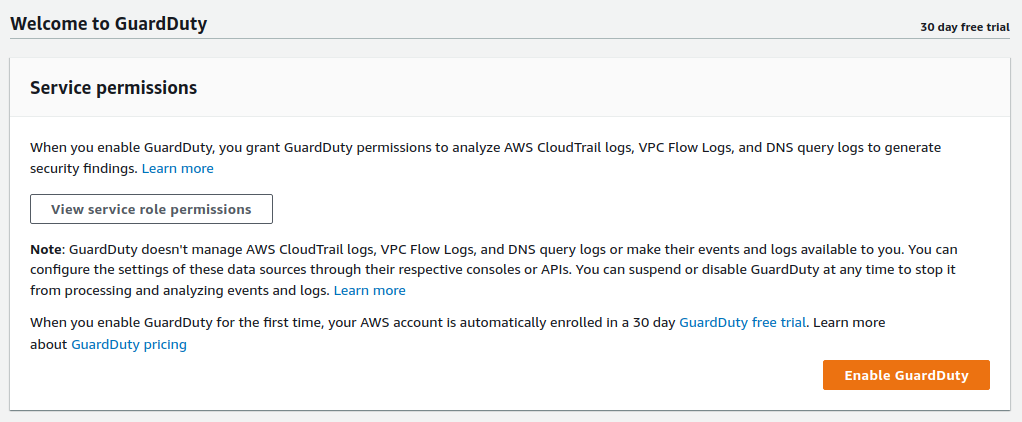
Click on "Get started" to configure Amazon GuardDuty for your selected region. Review the pricing and click "Enable GuardDuty".
# AWS Regions and Accounts
All of the AWS and Amazon services for security monitoring and posture management are specific to a single AWS account and region.
If you have AWS services running in multiple regions or in multiple AWS accounts, and you want to audit all of them using the Fraktal AWS Audit app, you should repeat the steps above and enable AWS Config, AWS Security Hub and Amazon GuardDuty separately for each region and account that you are interested in.
Decide what accounts and regions you are interested in and start with those. You can start small and turn on checks on a test account or a single region to get acquainted with the AWS and Amazon security services before enabling them on all accounts and regions.
However, remember that it is a common security problem to assume that you have resources only on a specific AWS account or region. The resources that you don’t even know about, let alone have monitoring on, are often the ones that enable attackers to gain access to your environment.
# Uninstalling the app
If you want to stop using the app, you can uninstall it and clean up the role delegation from your AWS IAM console.
Go to the Fraktal AWS Audit app page (opens new window) and click Uninstall.
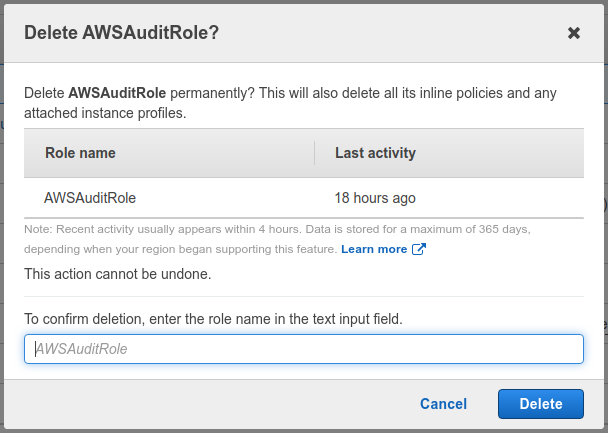
Clean up the app role from your AWS IAM console (opens new window).
Under the Roles (opens new window) section, find and select the role you created earlier (e.g. "AWSAuditRole"), select Delete and confirm deletion.
Turn off AWS Config, AWS Security Hub and Amazon GuardDuty in AWS Console for all of your accounts and regions, if you wish to stop using them.
That's it, you have successfully uninstalled the Fraktal AWS Audit app and cleaned up its configuration from your AWS installation.
